
Using Azure Bastion to access Azure VMs
Azure allows one to connect to an Azure VM without exposing the VM to the public with the help of Azure Bastion.
Once Bastion is deployed, you can connect to your VM in your VN just by the private address of the VM without any public IP, client software agent, or any special configuration.
In this article, let’s see how to use Azure Bastion can be used to connect Azure VMs.
Step 1: Here I am already on one of my pre-existing VMs. You can see you have three options to connect to a VM, That is RDP, SSH, and Bastion. Select Bastion from the list
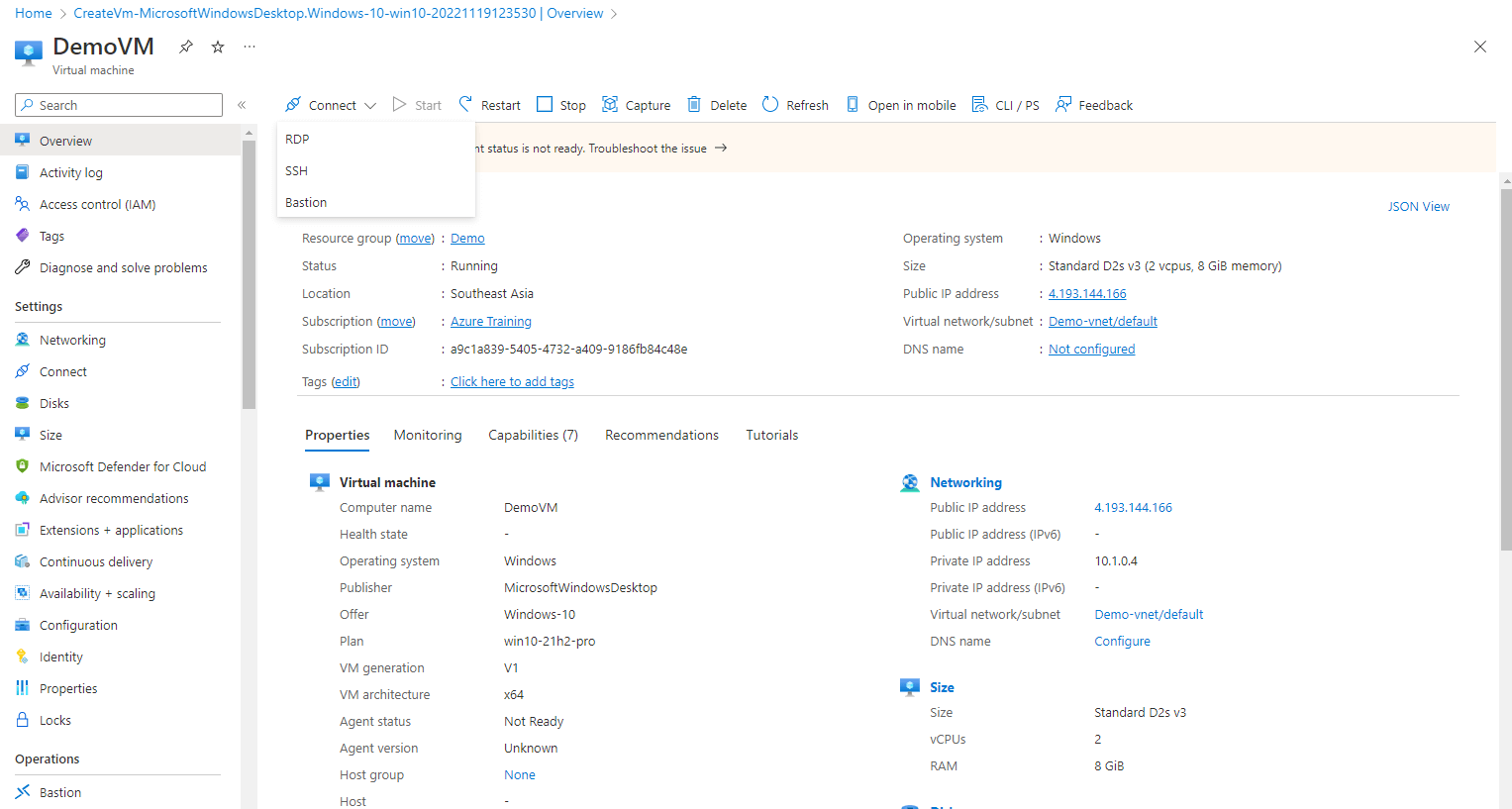
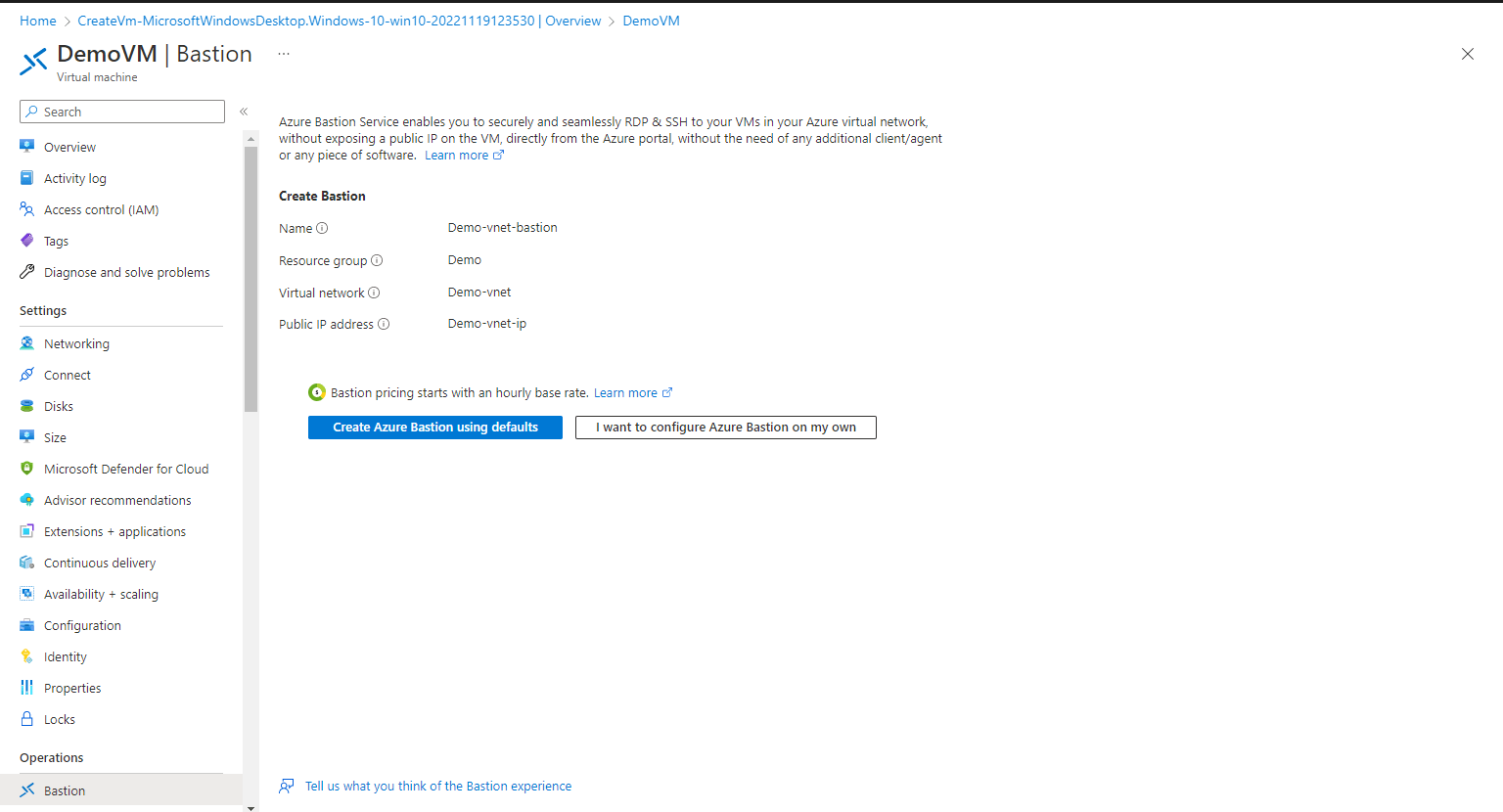
Step 2: Here the first time you are using Azure Bastion with your VM, you might have to configure the Bastion, either you can leave it to create by using defaults or select I want to configure Azure Bastion on my own
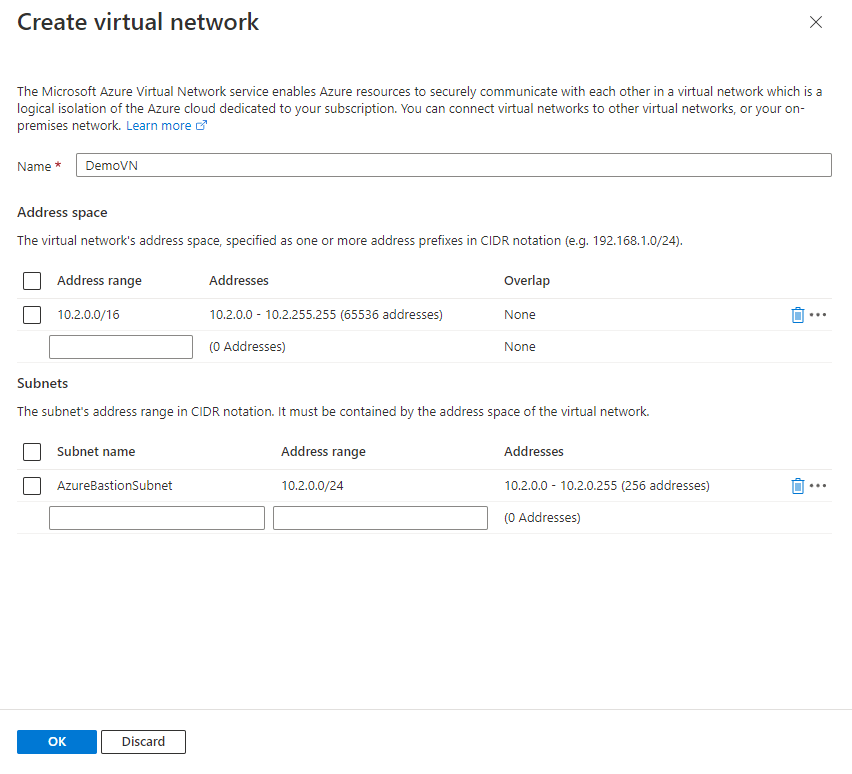
Step 3: On the Create a Bastion, Select, your Subscription, Resource Group, give a Name, and select the Region, Tier, and Instance Count. Here I am selecting the Instance count as 3, which defines how many users can access the VM via Bastion at the same time. Next select or create a VN and create a subnet with the Name as AzureBastionSubnet subnet must be at least /26 or larger.

Step 4: Leave the rest to defaults and click on Review + Create.
Step 5: Once the deployment is done, either you can connect via the same method, Connect–> Batison or you can select Batison from the left menu.
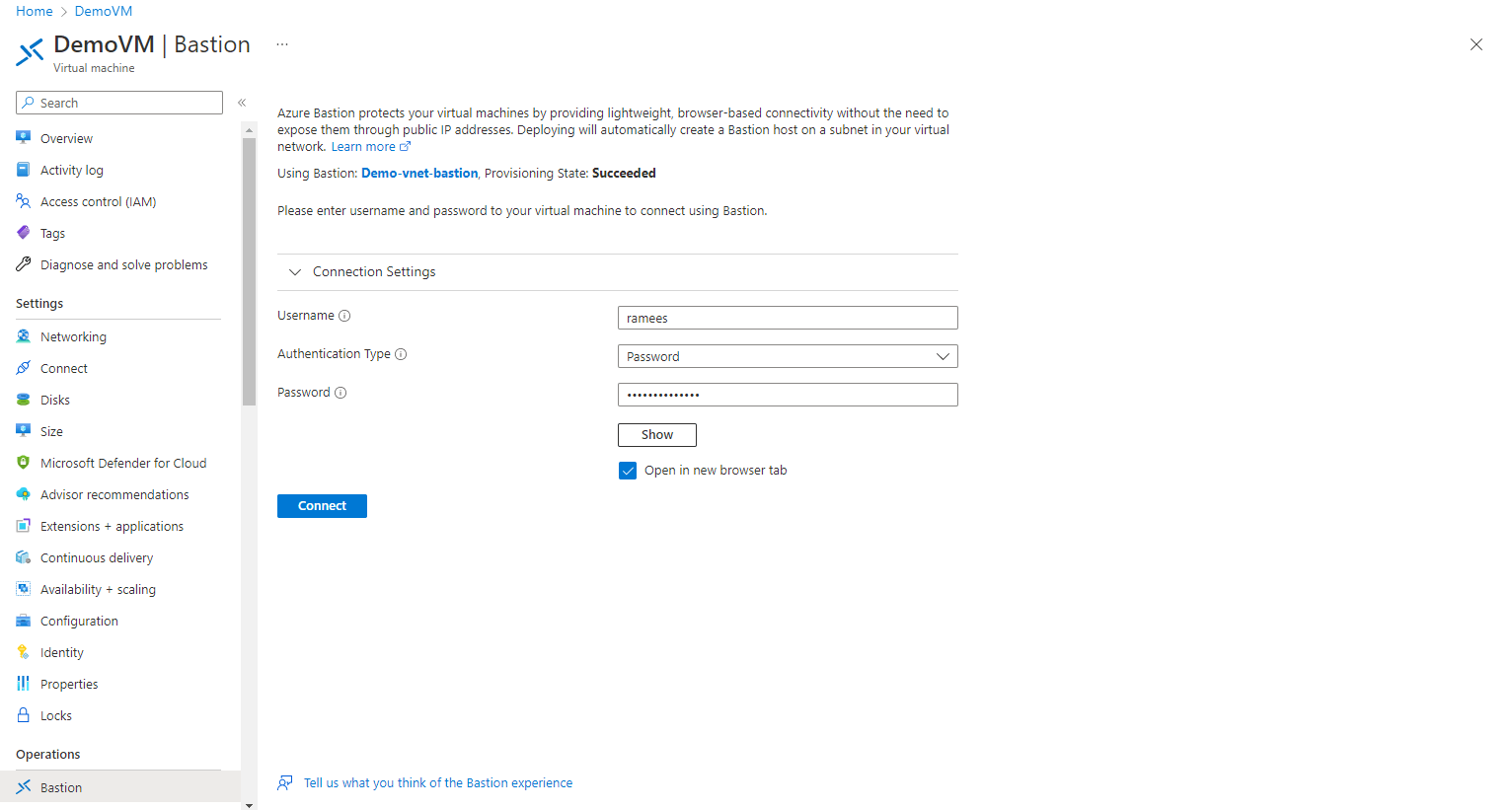
Step 6: Submit your username and password for the VM, and click on connect, if you want to open the VM in a new tab, you can leave the option checked.
As you don’t need a public IP address for connecting a VM via Azure Bastion, you can disassociate it from the VM if you are not using the public IP for anything else.
